Malware is a malicious software which is developed to perform activities which cause significant harm to the stored information, computer hardware or connected networks [1]. There are many types of malware such as trojans, adware, spyware, ransomware etc. The process of examining,
- how the malicious code works
- how to identify the malware
- elimination methods of malware are called ‘Malware Analysis’ [1].
Malware analysis can be achieved in two major methodologies. They are static analysis where the malware does not need to be executed by the malware analyst and dynamic analysis method that the malware analyst has to execute the analyst in a secure testing environment.
In order to demonstrate the procedures of these two types of malware analysis methods, TeslaCrypt ransomware has been selected. The original malware files have been downloaded from the following git repository.

Static Malware Analysis
Static malware analysis or code analysis is the process of analysing malware by inspecting the source code or the binary files of the malware without executing malware [2]. Advanced static analysis is simply a process of reverse-engineering the binary codes of the malware [1]. Simple static malware analysis can be conducted to a malware file by comparing the hash/signature values of the malware file with a reliable malware signature base. A static study for TeslaCrypt ransomware has been conducted using several techniques as below.
VirusTotal Malware Scan
VirusTotal is a free to use online malware scanner which currently owned by Google Inc. and partnered with over 70 antivirus organizations to provide real-time static malware lookup in a single user upload [3]. The following figure contains the VirusTotal scan result for the TeslaCrypt malware sample file. According to that 60 antivirus services out of 69 including the top-level antiviruses like AVG, Kaspersky, Bitdefender, F-Secure and Symantec have identified the sample file as malicious software.

Malware Fingerprinting through Hashing methods
In order to uniquely identify malware, the hash value of the malicious file can be generated via a hashing program. MD5 or Message-Digest Algorithm 5 is one of the most common hashing algorithms which is using in the computer security sector [1]. The hash value generated by the MD5 Algorithm can be used to lookup online malware scanners like VirusTotal without uploading the file to the scanner via the public network.
MD5 hash value of a file can be calculated using opensource tools like md5deep (command-line program) and WinMD5 (GUI program). The MD5 hash value of the TeslaCrypt malware sample file has been calculated using WinMD5 tool as below.

Hash Value of TeslaCrypt File: 209a288c68207d57e0ce6e60ebf60729
After searching the above hash value on VirusTotal’s Hash, IP and URL search option (www.virustotal.com/gui/home/search) the same result has been found as the following figure. Furthermore, SecureWorks, Inc. which is an information security subsidiary of Dell Technologies Inc. reveals that the above-calculated hash value belongs to the TeslaCrypt ransomware as below.

Apart from the above techniques, finding strings in the program code which can cause malicious activities and detecting packer through a tool like PEid can be counted as static malware analysis techniques.
Dynamic Malware Analysis
Dynamic malware analysis or behavioural analysis the way of studying the behaviours of malware by executing the malware program in an isolated test environment which is called Sandbox [2]. Based on this type of analysis, the analyst is able to identify functions, information flow and the network behaviour of malware in a practical approach [5]. Dynamic malware analysis can be easily conducted by using automated sandboxing tools like Cuckoo Sandbox, REMnux which simply create a virtualized environment to execute the malware.
The TeslaCrypt malware has been executed by using Cuckoo Sandboxing framework and presented the result as below.
Cuckoo Sandbox Online Report:

The most significant information which is revealed by the generated malware analysis report has been explained in the following pages.

As explained in Part A of the report .ecc is an encrypted file format which used to be only decrypted by the attacking party of TeslaCrypt. The above report reveals that the 2463 files in the sandboxing environment have been encrypted into the .ecc file format by the submitted malware program.

The attacker’s ransom message has been saved to the victim machines as HELP_TO_DECRPT_YOUR_FILES.txt. This message was previewed to the victim as a normal application window in the Cuckoo Sandbox machine. Alternatively, this massage can be prompt to the user in a blue colour interface where the victim doesn’t allow to even log in to his/her windows account.

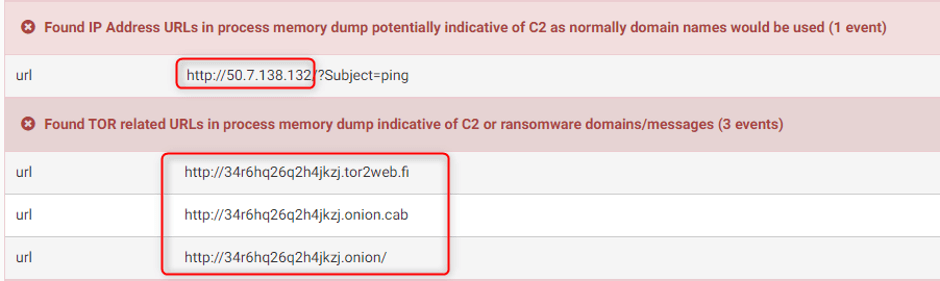
According to the following figure, TeslaCrypt malware has established TOR channels to securely control the victim machine which gives the ability to the attacker to hideously perform the decryption process in case the victim will pay the ransom. And also, the malware analysis framework has identified the command and control server of the malware as 50.7.138.132.


The ransomware has planted itself as a program that runs at the Windows Startup to have control over windows login to avoid access even the victim user account of the infected machine.
Changing desktop wallpaper to the image that contains the ransom message or something make the victims scared is a traditional setup of ransomware family. TeslaCrypt ransomware has also attempted to do that activity in the sandboxed Windows environment. However, it was not succeeded in the setup sandbox according to the following report identifier.

Wrapping Up
Conducting code inspection (Static Analysis) for these malware sample files and analysing the behaviours of the malware by executing them in a secure environment called sandbox (Dynamic Analysis), enables malware analysts to identify the malware infection and develop necessary security patches to mitigate these malware infections.
References
[1] M. Sikorski, Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software, No Starch Press, 2012.
[2] D. Distler, “Malware Analysis: An Introduction,” 12 February 2008. [Online]. Available: https://www.sans.org/reading-room/whitepapers/malicious/paper/2103. [Accessed 02 September 2019].
[3] F. Lardinois, “Google Acquires Online Virus, Malware and URL Scanner VirusTotal,” TechCrunch, 7 September 2012. [Online]. Available: https://techcrunch.com/2012/09/07/google-acquires-online-virus-malware-and-url-scanner-virustotal/. [Accessed 02 September 2019].
[4] Dell SecureWorks Counter Threat Unit, “TeslaCrypt Ransomware,” SecureWorks, 12 May 2015. [Online]. Available: https://www.secureworks.com/research/teslacrypt-ransomware-threat-analysis. [Accessed 22 July 2019].
[5]M. Egele, T. Scholte, E. Kirda and C. Kruegel, “A survey on automated dynamic malware-analysis techniques and tools,” ACM Computing Surveys (CSUR), vol. 44, no. 2, 2012.




