
Data Storage is a major requirement for most of the businesses in the modern digital edge. The main reason for that fact is the usage of IT-based systems and digitalized workflow in the business environment. The rapid growth of the technology has always approached more efficient, reliable and cost-effective data storage model. Cloud Computing is one of the cutting-edge technology that has satisfied the necessity of powerful data storage infrastructure to small businesses and enterprises. However, the security aspect of the cloud is an argumentative topic in industrial and academic environments.
Introduction to Cloud Computing and Cloud Security
Cloud computing is a revolutionary concept and a mechanism that has been recorded as a milestone in computer networking history. Virtualization or the technology of creating and managing a pool of shared hardware resources that act as a remotely accessible single machine is the fundamental technology of cloud computing.
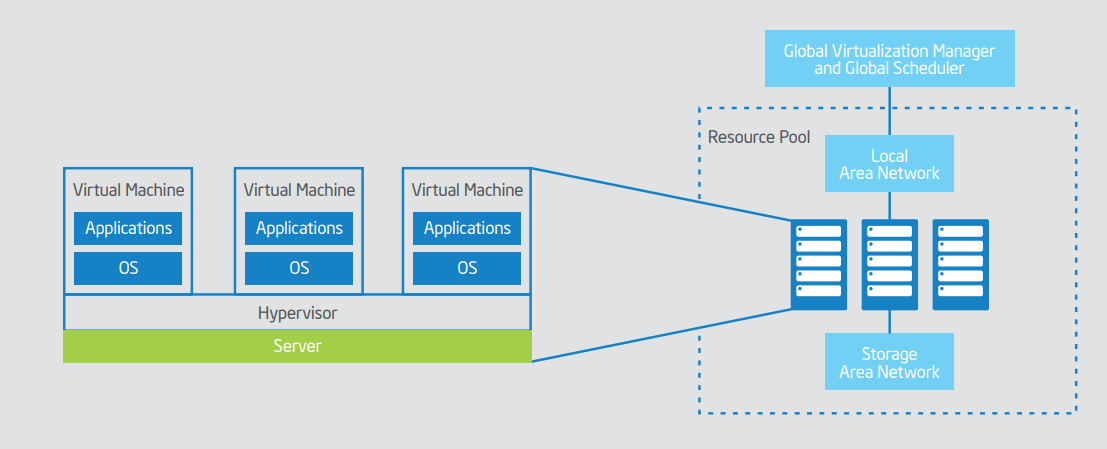
According to Xing and Zhan (2012), the idea of cloud computing has been originated from the 1960s and the word “Cloud Computing” involved to the story in 1997 by Prof. Ramnath Chellappa. Cloud computing allows users to access and manage virtualized remote hardware resources through the internet and it gives many services to the user. Such as,
- Software as a service – SaaS (Eg: G Suite, Office 365, Netflix, Zoho Apps)
- Platform as a service – PaaS (Eg: Google App Engine, Apache Stratos)
- Infrastructure as a service – IaaS (Eg: Amazon Web Services, Google Cloud, Digital Ocean)
Furthermore, University of Illinois (2018) has mentioned that there are Cloud Delivery Models are categorized according to the structure of infrastructure as public, private and hybrid.
Server virtualization also refers to cloud computing. Specifically, that can be defined as the technique behind configuring the pooled resources (servers). However, Winn (2014) has stated that server virtualization is the process that a human administrator takes place for configuring the resource while cloud computing is using an automated process of configuration using Application Programming Interface (API).
Cloud Computing provides many advantages to the user than traditional data centres. Some of them are,
- Increased Speed
- Rapid Elasticity or Scalability
- Measured Service
- On-Demand Self Service
- 24/7 Availability
Even though cloud computing provides many advantages, the organization or the individual who uses cloud hosting should be considered the safety of using these cloud services. At that point, the term “Cloud Security” took the attention of cloud computing community and introduce countermeasures for the vulnerabilities of Cloud Computing Networks and produced many job opportunities to IT security experts to take part in the cloud computing industry.
Cloud Security Threats
Violino (2018) has clearly identified 12 main types of threats to cloud computing in the modern era. They are,
- Data breaches (stealing sensitive data from the cloud storage)
- Unauthorized access/account hijacking
- Misusage of Application Programming Interfaces (APIs)
- Vulnerabilities of the systems and associated technologies
- Malicious insiders
- Data losses
- Denial of service attacks (DOS: The system will not be able for the authorized users)
Even though there are many identified challenges for cloud infrastructures as above, Cloud environments can easily have secured via cloud security techniques which are mentioned in the Methods to protect Cloud environments section. However internal attacks like Malicious insiders are hard to mitigate without good business policies.
Recent Cloud Security Attacks
| Company | Year | Attack | Result |
| Microsoft | 2010 | Microsoft Office 365 had a configuration issue and non-authorized users could be able to access Microsoft offline address book that contains its employee contacts. | Microsoft has solved the error within 2 hours and only a few users were affected. |
| Dropbox | 2012 | The attackers have stolen over 68 million user account data including email addresses, passwords that equal to 5GB of data storage. | The attackers have sold the stolen data to the dark web market. Dropbox has carried out a user-based password reset as a solution for this data breach. |
| National Electoral Institute of Mexico | 2016 | Over 93 million voter registration records were compromised and publicly available. | The organization has decided to leave their cloud service provider Amazon Aws and store their confidential data within their own infrastructure. |
| 2012 | 6 million user sensitive data was stolen and posted on a Russian web forum. | LinkedIn has rest passwords of the affected users and introduced two-way authentication for its users. | |
| Apple iCloud | 2014 | Private photos of a celebrity that has stored in Apple iCloud were leaked to the internet. | Apple has made a new password policy and introduced account activity log notification to its users. |
(Bradford, 2018)
Methods to protect Cloud environments
Cloud Infrastructure Security
In a cloud environment, managing the infrastructure is a responsibility of the cloud service provider. As a result of that, the user of a SaaS, PaaS, or even IaaS won’t be able to directly get involved in the cloud infrastructure security management. The security audits and the support of technical experts at the infrastructure end usually protect the data of users. Especially during complex migrations tasks like VM Migration or Tenant to Tenant Office 365 Migration. However, the infrastructure is not a real asset of the user. This is one of the most sufferable facts by being a cloud infrastructure user.
Malik, Gupta and Kaushik (2014) have stated that infrastructure security should be configured or manage in-network level, host level and application level. In Network level, the infrastructure should be able to provide a dedicated logical environment to each user to ensure data confidentiality and data integrity also with encryption in transit across the network with Transport Layer Security (TLS). Hypervisor security must be handled in host level and Applications should be updated in order to minimize application-level vulnerabilities.
DDOS Mitigation in the Cloud
24/7 availability is one of the best advantages of cloud computing. As explained by AWS (2016) Denial of Service Attack (DOS) is a threat that can directly affect to the availability of an online service to the authorized users by sending invalid data packets to the server continuously. A well-organized DOS attacks that operated for multiple locations are called as Distributed Denial of Service Attacks (DDOS). These attacks can completely shut down the network for a time and the user may have to pay for the misused resource usage.

An intelligent cloud computing network can easily identify and mitigate DDOS attacks automatically without any user involvement. The DDOS Resilient Cloud Architecture of popular cloud hosting service Amazon Web Services can be represented as below.

DDOS mitigation has become an essential security mechanism which should be implemented for any kind of cloud server in the modern internet era. The security features of modern Cloud Security tools like Cloudflare defend the cloud users and resources from all types of network level threats including DDOS attacks.
Data Encryption in the Cloud
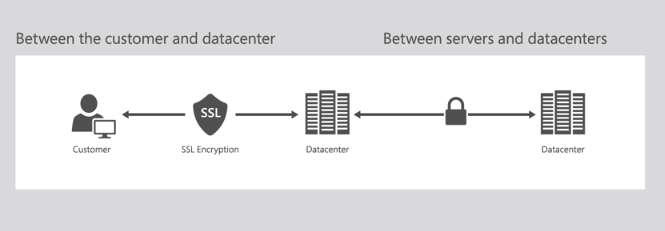
Data encryption is a mechanism that use cryptography to transform or encode real data into another data format that can be only read by the authorized users. Data encryption concepts apply to the cloud in two separate ways. They are encrypting stored data in the cloud servers and encrypting communication within or among the networks.
Lord (2016) has clearly mentioned that data encryption in the cloud is also called Cloud Encryption. This method protects data from data breaches because the attacker doesn’t have the key to decrypt the encrypted data. Nowadays, Data encryption is the main requirement of any data storage that is regulated by internet policies such as HIPAA, PCI DSS, SOX etc.
Data Encryption should happen in data communication to avoid attacks such as the man in the middle and phishing. According to Microsoft (2018) encryption applies to data transformation in a cloud when the client is communicating with the cloud server and data movement among servers in cloud data centre. Secured Socket Layer (SSL) can be used to protect client communication with the cloud server.
Monitoring and Logging in the Cloud
Monitoring and recording activity logs are also needful in a cloud environment and it is very easy to implement a monitoring system on top of the cloud software services stack. As mentioned by AWS (2018), Activity logs easily identify and notify about unauthorized access, resource failure, unnatural activity.

Authorization and Access Control in the Cloud
Cloud resources are assessable via the internet. This is the biggest security challenge in cloud computing. Reason for that is a person who can steal the credentials of an authorized person can access the cloud storage without any problem. Younis, Kifayat and Merabti (2014) have stated that role-based access control cannot fulfil the safety of a cloud network. Multifactor Authentication is a best practice for security in this perspective.

Conclusion
Cloud computing has changed the whole networking industry within a few years to fast, efficient, always online data infrastructure. Although, cloud computing has several drawbacks in the security. Mainly, the users store their data in an unknown physical environment. To avoid this issue in trustworthiness and other security risks the report suggests focusing on cloud infrastructure in 5 solutions and it also suggests best practices that have used to overcome the cloud problems by popular cloud service providers in the industry.
References
- Amazon Web Services. (2018) AWS CloudTrail. [Online] Available at: https://aws.amazon.com/cloudtrail. [Accessed: 20th March 2018].
- Amazon Web Services. (2016) AWS Best Practices for DDoS Resiliency. [Online] Available at: https://d1.awsstatic.com/whitepapers/Security/DDoS_White_Paper.pdf. [Accessed: 24th March 2018].
- Bradford, C. (2018). 7 Most Infamous Cloud Security Breaches – StorageCraft. [online] StorageCraft Technology Corporation. Available at: https://blog.storagecraft.com/7-infamous-cloud-security-breaches/ [14th March 2018].
- Duddington, M. (2017) Cloud Identity Overview – Part 2 (Authorisation). [Online] Available at: https://blogs.msdn.microsoft.com/oncloud/2017/06/22/cloud-identity-overview-part-2-authorisation/. [Accessed: 19th March 2018].
- Intel. (2013) Planning Guide: Virtualization and Cloud Computing. [Online] Available at: https://www.intel.com/content/dam/www/public/us/en/documents/guides/cloud-computing-virtualization-building-private-iaas-guide.pdf. [Accessed: 19th March 2018].
- Lord, N. (2016) What is cloud encryption?. [Online] Available at: https://digitalguardian.com/blog/what-cloud-encryption. [Accessed: 19th March 2018].
- Malik, V., Gupta, S. and Kaushik, J. (2014) Network Security: Security in Cloud Computing, International Journal of Engineering and Computer Science, Vol. 3, pp: 3643-3651. [Online] Available at: http://www.ijecs.in/index.php/ijecs/article/view/38/30. [Accessed: 20th March 2018].
- Microsoft. (2018) Data Encryption in OneDrive for Business and SharePoint Online. [Online] Available at: https://support.office.com/en-us/article/data-encryption-in-onedrive-for-business-and-sharepoint-online-6501b5ef-6bf7-43df-b60d-f65781847d6c. [Accessed: 20th March 2018].
- Winn, O. (2014). Differences Between Cloud Computing and Virtualization. [Online Video]. 29 January 2014. Available from: https://www.youtube.com/watch?v=14KJoDs6reg. [Accessed: 21st April 2018].
- University of Illinois. (2018) Types of Cloud Computing: Private, Public, and Hybrid Clouds. [Online] Available at: https://cloud.illinois.edu/types-of-cloud-computing-private-public-and-hybrid-clouds. [Accessed: 19th March 2018].
- Violino, B. (2018) The dirty dozen: 12 top cloud security threats for 2018. [Online] Available at: https://www.csoonline.com/article/3043030/security/12-top-cloud-security-threats-for-2018.html. [Accessed: 12th May 2018].
- Xing, Y. and Zhan, Y. (2012) Virtualization and Cloud Computing. In: Zhang Y. (eds) Future Wireless Networks and Information Systems. Lecture Notes in Electrical Engineering, vol 143. Springer, Berlin, Heidelberg
- Younis, A., Kifayat, K. and Merabti, M. (2014) An access control model for cloud computing, Journal of Information Security and Applications, Vol. 19, pp: 45-60. [Online] Available at: https://doi.org/10.1016/j.jisa.2014.04.003. [Accessed: 30th March 2018].




